Electronic Card Access Control Systems
Toronto

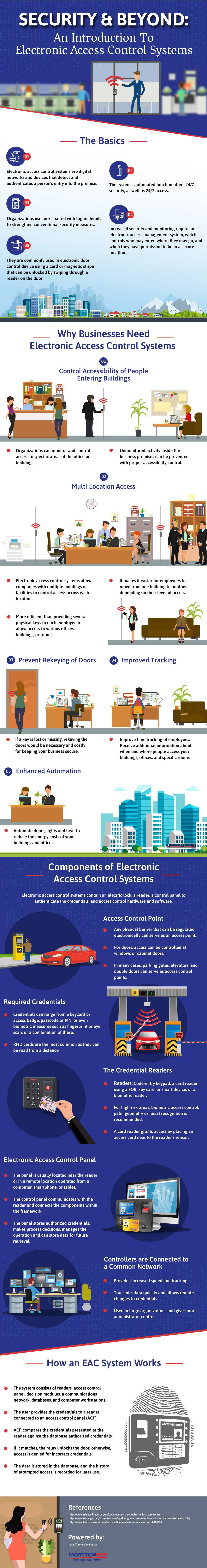
Keeping your organization safe is always top of mind. The more sensitive your operation, the more secure it must remain. Using electronic access control systems (EAC) provides the protection you need in the simplest and most accessible manner. They offer digital networks and devices designed to detect and authenticate entry onto your premise. These systems effectively operate 24/7 with customized access provided based on the person entering your facility. You can use the system paired with log-in details to enhance your security measures. You will have total control over who enters every area within your facility, and determine who is allowed access to each area. You can even limit access to certain areas based on the time and day of the week. With the onslaught of COVID-19, having touchless security and entry options are more important than ever. Combining hygienic entry options in hand with a security system that allows you to dictate permission-based entry creates a state-of-the-art security system ideal for any organization.
Combined Entry and Security
Your electronic access control system is highly customizable, allowing you to use them with other lock and security measures. Most commonly, they are partnered with electronic door control devices unlocked using an RFID card, PIN code or biometric scans. Today, touchless options are in high demand to prevent the spread of viruses like COVID-19.
The Benefits of Electronic Access Control Systems
There are many reasons you need an electronic access control system:
- Control: You have better control over who enters your organization and the areas they can access. You can monitor and control access depending on the clearance for each visitor or employee. You can also prevent unmonitored activity inside your premises based on accessibility control.
- Multi-location Access: COVID-19 has made it more difficult to ensure that essential employees access unique facilities. Using electronic access control systems, you can control multiple buildings from one system. Introducing touchless and wave to open options reduces touchpoints throughout your facility while making it easier for employees to move from location to location based on their approved access level.
- Avoid Rekeying of Doors: A lost or missing key is costly, as it requires rekeying the doors. Your EAC makes rekeying unnecessary.
- Improved Tracking: Your system allows you to see who is on your premises, where they are and when they enter and leave to look for potential security and performance issues.
Perhaps best of all, you can integrate your system with various business apps and devices. This allows you to use your access control system for functions such as visitor management, lighting and room booking.
Components of Electronic Access Control Systems
Your electronic access control systems consist of:
Access Control Point (Entries)
Manage and create regulated physical barriers for secure access points, including doors, parking gates, storage cabinets and elevator floors, where access is restricted.
Credentials
Credentials include:
- RFID key cards and fobs: These are the most hygienic form of access control. You can choose:
- Proximity cards to communicate using low-frequency fields and provide no encryption.
- Contactless smart cards communicate using high-frequency fields.
- Swipe cards are considered less secure than RFID cards because they’re usually not encrypted and are easy to clone.
- PIN code: PIN readers use PIN codes to grant access, but are not recommended for areas that require high security.
- Biometrics: This would include entry via fingerprints or palm veins, but present a greater possibility to malfunction in dusty or humid environments.
- Mobile: Employees use their smartphones to make unlock requests by touching the reader.
You can choose to use a single type of credential or a combination suited to your specific needs.
Credential Readers
Credential readers are installed near the entries to allow staff or visitors to use their credentials to send the inputs to the Access Control Unit (ACU) using a wired or wireless connection. High-risk areas are more secure using biometric access control, palm geometry or facial recognition.
Electronic Access Control Unit
The ACU is used to receive the credential data from the reader. Once the proper credential is used, access is provided, and the ACU will unlock the door. The ACU can make processing decisions and manage data such as credentials, PINS, and other security features.
Locking Hardware & Access Control Software
This is the functioning electromagnetic locks, push bars, and other electrified hardware used to configure entries. It is managed using access control software, allowing the information to be defined in the application syncs with the ACU to determine if access should be granted.
How an EAC System Works
While all these parts and functions might seem complicated, in its most basic form an EAC system is quite simple. It works in the following way:
Step 1 – Authentication: First, the user must present their credentials to the access points’ reader. The reader sends the data to the ACU, so it can determine if the credentials meet the access point’s requirements.
Step 2 – Authorization: Next, the ACU determines whether the system recognizes the user and if they have the right kind of credential to trigger entry. This process can include a vast series of data, including:
- If the user has access to the entry that they’re trying to unlock
- If they are using the predefined allowed credential types and trigger types
- If they are making the unlock request within any schedules defined on the entry
It will also ensure that the other restrictions, such as a system lockdown, are not currently triggered.
Step 3 – Access: Once authorization is complete, commands are sent from ACU to the door-locking hardware to unlock the entries.
Step 4 – Manage: Administrative software is used to sync automatically with internet-connected ACUs for adding or removing entries, user credentials, schedules, and alerts.
Step 5 – Audit: Your organization’s administrators can generate reports for access logs, including both user activity and entry activity, by auditing the access control system. This ensures there are no issues with accessing entries, and the system is working correctly.
Despite the many steps involved in entry and authentication, it all happens almost instantly, providing quick access for authorized employees or visitors. The EAC system is highly customizable, efficient, and hygienic, providing any organization large or small with a dependable access process.







